Is your company ready to take its first step towards SOC 2 compliance? Are clients asking for it and leaving you in a rush to figure out what to do? It is not as complicated as you think—especially when you use the right SOC 2 compliance automation software to guide your process.
What Does SOC 2 Compliance Mean?
The AICPA has developed a standard for compliance called the SOC 2. Potential clients use it to determine whether a service organization implements practices related to data security. The report is flexible and useful for potential clients to judge the data security posture of the service provider.
It relies on five Trust Service Criteria (TCAs), but only security criteria is compulsory. Availability, processing integrity, confidentiality and privacy are optional criteria which a company can opt for based on project requirements or client needs.
SOC 2 can be a report on the design of policies and processes relating to data security. This Type I compliance relies on a single audit. The Type II audit is more exhaustive with a long period of multiple audits. So it focuses on the day-to-day implementation of the data security protocols.
Benefits Of Being SOC 2 Compliant
The process of SOC audit is lengthy, laborious and costly. Yet, the company has several incentives in becoming SOC 2 compliant as the audit is rigorous and trusted across the industry.
The Perks
The process SOC 2 compliance rejuvenates the data security posture of companies as it incentivizes adoption of the best security practices. This helps the company to defend its clients’ data from potential attacks.
Although there is no actual certificate, the report generated after the audit reassures potential clients that the company can protect their data. The validation from the AICPA works better at inspiring confidence in customers than any certificate.
Since the compliance is flexible and there are many criteria, clients can look at specific parameters relevant to their project. At the same time, companies can also tailor their compliance to best prepare themselves for the need of a specific project.
Who conducts the SOC 2 Audit?
The AICPA has strict guidelines on planning and execution of SOC audits. Only certified third party accounting firms (Certified Public Accountants) perform SOC 2 audit. Other professionals with relevant skills can gather the data, but the CPA organization presents the report. Other CPAs review the report.
Do you need the SOC 1 or the SOC 2?
SOC 1 focuses on the security of financial data for those companies which handle them. SOC 2 encompasses overall data security. So their purpose is different. As a result the procedures and ultimate uses are also different. If you want to give an audited account of your data security protocols and their implementation then SOC 2 is the audit for you. Partners and clients get the most use out of this technical document.
Checklist To Fulfill SOC 2 Criteria
Of the five TSCs, security forms the common basis for all the criteria. So a company must conform to the security criteria to pass the SOC 2 audit. Security principles are focussed at maintaining authorized access to prevent attacks and misuse of data. The four-step checklist form the basis for companies to device their security protocols and procedures:
- Step 1 – Restricting access both logically and physically maintaining authorized access to data
- Step 2 – Having policies in place for managing changes in the IT infrastructure
- Step 3 – Monitoring of systems to detect anomalies and address security events
- Step 4 – Identifying weaknesses that can be exploited by hackers and addressing the risk they pose to data security.
Other Criteria For SOC 2 Compliance
Besides complying with the security criteria of the SOC 2 audit, companies must also comply with other criteria. While these factors impact data security, the company can address them based on project needs once they have met the basic security criteria. The other principles in the TCAs are follows:
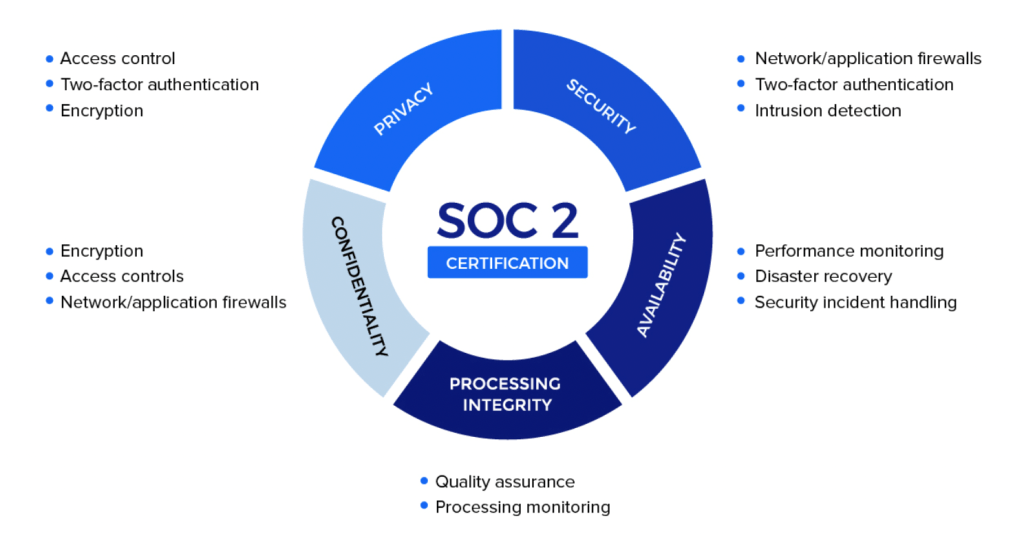
- Availability
It ensures customer access to data matches agreed upon standards.
- Processing
The integrity ensures that all financial data is secured during transactions.
- Confidentiality
It ensures that sensitive personal information of clients and their customers is protected and secured at all stages of interaction with the data.
- Privacy
It ensures that the customer is made adequately aware of the collection and use of private information.
The complex procedures of SOC 2 compliance become more difficult if they are managed poorly. With expertise and a clear plan, it becomes a lot easier. Sprinto can provide this service for your company. It will also bring essential tools which will help automate the entire process making it cheaper, hassle-free and error-free.

